

Security
Enterprise Class Security As Standard
Irrespective of the company size, budget, and function or activity, vulnerability doesn’t really change – the shotgun approach to delivering malware affects us all and can engulf or overwhelm systems.
A structured approach to cover multiple delivery methods is required, cleaning and filtering our communications, protecting our perimeters and closing down our gateways.
Firewalls
Correctly configured and suitable levels of firewall are a must at the perimeter of out networks. We may need to meet a compliance standard. Sometimes a simple solution is the best and most appropriate. Decisions can be made based on what is behind the device on the private network, what device, what data, humans? all require different considerations and different solutions. Advanced, next generation, firewalls give us the ability to gain insight to the network traffic, and to set parameters allowing or disallowing categories, applications, data and files, in or out.
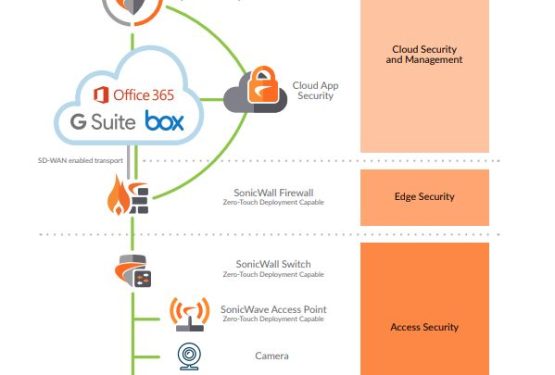
Mail and Internet Filtering
Threats and malicious software, virus’s, enter systems in multiple ways. we need to protect against these, blocking the entry points, but without detrimental effect on productivity. Removeable drives, webpages, emails, smartphones, all may need some control to pave the way to a secure environment. We use advanced features to track links in emails, and remove malicious or unpleasant content. We can use our advanced firewalls to monitor the information coming from the Internet, and to interrogate downloads, even when encrypted, before they are delivered to our users.
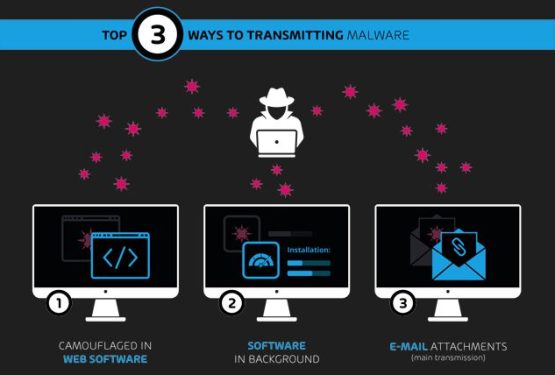
Humans
Intentionally or not, most security issues start with a human! CEO Fraud has people targeting individuals, and they do huge amounts of research, social media profiles etc to get the scam in front of the right person, and to get that payment through to the wrong bank account.
Data theft should also be considered. Why did Tony just copy 400 files to a USB Stick? Maybe we should investigate?
Passwords, 2 Factor Authentication (2FA), Biometrics, Tokens, Are they strong, and appropriate for the task in hand.
Experts in
System Design
- We will advise, design, supply and install, once the right solution has been identified.
- We use best in class equipment, software and services.
- Bespoke software? we will liaise with the third parties to ensure consistency.
- Supply chain issues? We have trusted distributors, with long established relationships, to get you the right kit, when you need it.
Network Security
- Install fully managed firewall solutions from the top vendors.
- Secure networks, secure data, manage staff and external access.
- Prevent, dont cure.
- Meet industry standards, achieve compliance.
Data Protection
- Protect the business against the unknown, or the unexpected. We can prepare and provide your Business Continuity and Disaster Recovery strategy.
- Clean the environment – we use advanced software products and services to ensure only the items and communications you need enter the workplace.
- Never assume its being backed up by your provider. And never assume its in the UK – Data Protection Regulations require this. We backup to our own, owned storage.
- Using suitable kit will give you the warranty, and peace of mind you require. No-one wants a warranty that takes 3 weeks to get your laptop back to you – they want it tomorrow – working!
Connectivity
- We provide business class connectivity across the board – and we answer the phone when you call. try it..
- Broadband, Fixed line (for a while), FTTC, FTTP, DIA, we can provide best in class, or best available at a competitive rate.
- Short term contracts – no problem, event connectivity? We understand the requirements for a modern business and that things move, fast. we can connect you for a few weeks, without a contract that lasts months or years.
- Staff on the road or at home need connecting to the office, quickly and securely. We can cover it and have it all in one place, and under control.
Modern Communication
- 18 years on VoIP gives us the experience we need to sort your telephony.
- Choose handsets, choose system, choose billing model that suits you, choose not to have a never-ending, support and maintenance contract that is 5 times more expensive that the system was in the first place.
- Own the kit, it lasts for years and years, why replace it every few years in this world we need to think of more that just the function. Our way is greener, and more sustainable.
- Get what you were promised, if we say it will work, it will. If your plan wont work, we’ll tell you!
Support
- When you call, we answer the phone. If you want technical, you get through to technical, not reception.
- We monitor and manage – reports come to us, not you. (Unless you want them obviously) We proactively act on the issue, hopefully before you are aware it exists.
- End user support – remotely to the desktop – irrespective of location. Goes without saying really.
Case studies
View All
Case Study – Campus WiFi Networks
Supplying Internet to the south wests most prestigious holiday parks needs a specialist, specific technology, planning and deployment.

Multi Site – IP Telephony
With many of the sites open to the public, we needed to make sure that the deployment could be staged, and that it could be carried out with a seamless…









